
ESET Threat Intelligence Service
Extend your security intelligence from local network to global cyberspace
Sorry, this product is no longer available, please contact us for a replacement.
More pricing below, click here!
Overview:
Nowadays it’s important for companies to get intelligence from the widest possible range of sources in order to adapt proactively to the ever-changing security environment. Targeted attacks, advanced persistent threats (APTs), zerodays and botnet activities are difficult to discover for security engineers with access only to information from within their own company networks— a bigger picture and deeper intelligence is needed.
ESET Threat Intelligence closes the gap between the cybersecurity information that security engineers get from their own networks and the cyberspace intelligence that ESET collects worldwide. It uses information gathered from more than 100 million sensors and sent to ESET’s Cloud Malware Protection System via ESET LiveGrid, then channeled through ESET’s multiple award-winning ESET R&D centers, which are distributed worldwide and focus solely on cybersecurity. This allows ESET to provide its unique knowledge to customers to help them understand and manage business risk and turn unknown threats into known and mitigated threats, thereby improving the effectiveness of their defenses.
Global knowledge for your security
Targeted attacks, advanced persistent threats (APTs), zero-days and botnet activities are difficult to discover for security engineers who can only access information within their own company networks. For effective protection, you need deeper intelligence with a broader reach.
How ESET Threat Intelligence can help you
Cloud-based ESET Threat Intelligence closes the gap between the cybersecurity information that security engineers get from their own networks and the cyberspace intelligence that ESET collects worldwide.
With ESET Threat Intelligence, you get detailed:
- Targeted malware early warning
- Botnet activity report
- Automated sample analysis
ESET's global early-warning system
Our cloud-based detection and prevention system, seeded by more than 100 million sensors worldwide, provides a unique base for the immediate detection of and response to new, unknown or advanced threats.
Get early warnings about threats in the wild and harden your security proactively.

Human expertise, backed by machine learning
The use of machine learning to automate decisions and evaluate possible threats is a vital part of our approach – but it’s only as strong as the people who stand behind the system.
At ESET’s R&D centers, distributed around the world, world-class security researchers pool intelligence to ensure the best round-the-clock threat intelligence.
Features:
Real-time Data Feed and API
ESET Threat Intelligence Data Feeds utilize widely used STIX/ TAXII format for threat intelligence information exchange. This makes it easy to integrate with existing SIEM tools of security service providers and deliver the latest information on the threat landscape, especially botnets, to predict and prevent threats before they strike. In turn, this proactively strengthens the security of their end customers. Moreover, ESET Threat Intelligence API is available for automation of reports, YARA rules and other functionalities with any other systems used on the customer side.
Targeted malware report
Our targeted malware report keeps the user informed about a potential attack that is in preparation, or an ongoing attack aimed specifically against their organization. Custom rules can be set up using YARA to obtain the company-specific information that security engineers are interested in. Based on the report, the user gets valuable details about ongoing or possible targeted malware campaigns, including the number of times they have been seen worldwide, URLs containing malicious code, malware behavior on the system, where it was detected, and more.
Botnet activity report
This delivers regular reporting and quantitative data about identified malware families and variants of botnet malware. Classified according to malware type, the report provides a list of known Command and Control (C&C) servers involved in botnet management, as well as a list of targets of this malware.
Automated sample analysis
The more you know the less you believe. A custom report based on the submitted file or hash provides valuable information for fact-based decisions and incident investigation.
Extra security, even if you're not a current ESET customer
Security analysts recommend combining a range of security approaches in order to minimize the potential weaknesses that can arise from using a single-vendor security solution. ESET Threat Intelligence does not require that ESET endpoint or server solutions are deployed on the user’s network. This means that it can be used by non-ESET customers as an additional layer of security to help alert them to imminent malware campaigns or targeted threats about which their existing security vendor may not be aware.
How It Works:
Cloud Malware Protection System
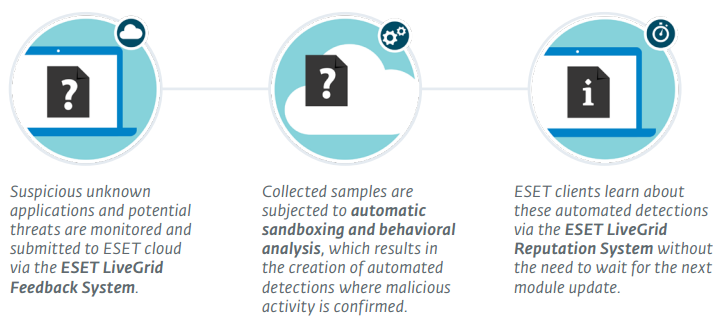
The ESET Cloud Malware Protection System is one of several technologies based on ESET’s LiveGrid cloud system. Possible threats are monitored and submitted to the ESET cloud via the ESET LiveGrid Feedback System for automatic sandboxing and behavioral analysis.
Reputation & Cache
When inspecting a file or URL, our products first check the local cache for known malicious or white-listed benign objects. This improves scanning performance. Afterwards, our ESET LiveGrid Reputation System is queried for the object’s reputation.

DNA Detections
DNA Detections are complex definitions of malicious behavior and malware characteristics. While malicious code can be easily modified or obfuscated, object behavior cannot be changed so easily. Therefore, DNA Detection can identify even previously unseen malware that contains genes that indicate malicious behavior.

Documentation:
Download the ESET Threat Intelligence Datasheet (PDF).
Pricing Notes:
- Pricing and product availability subject to change without notice.
